What is MOTW?
Mark-of-the-Web is a security feature in Windows that flags files which are downloaded from the internet as the file is downloaded from the internet and it could be malicious therefore, it should be treated with caution.
MOTW flags the files that are downloaded from the internet with an Alternate Data Stream named ‘Zone.Identifier’.
You can view the ADS using the following command
> dir /R
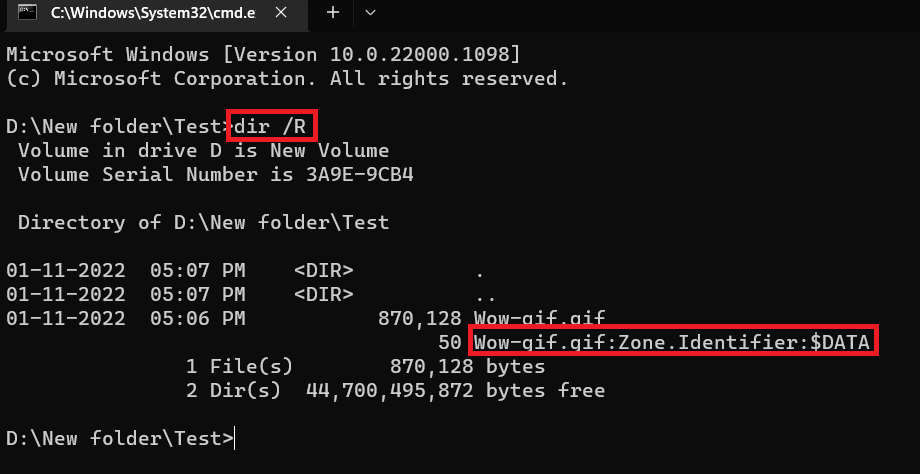
The contents of the ADS can be directly viewed with Notepad as shown below.

ZoneId values used in a Zone.Identifier ADS:
0: Local computer
1: Local intranet
2: Trusted sites
3: Internet
4: Restricted sites

Microsoft Office uses the MOTW flag to decide whether the file should be opened in Protected View (macros disabled) or not.
Windows Zero-day MOTW bypass?
Recently, the HP threat intelligence team reported that the threat actors are distributing .js files and are infecting devices with Magniber ransomware.
These files were analyzed by a senior vulnerability analyst Will Dormann. He discovered that these files were signed with a malformed key and it was signed in this manner that even though the .js file was downloaded from the internet, flagged as MOTW, it would not receive the security warning and the script would execute automatically.
The GIF below illustrates that “calc.js” does not have a malformed key and it gives a security warning, on the other hand “cal-othersig.js” has a malformed key and it directly executes the script with no security warning.

This .js file uses .net to .js technique which enables the attacker to load a .net executable in memory which means that the ransomware does not need to be saved to disk.
What is Magniber ransomware?
Magniber ransomware is a single-client ransomware family which is known to demand $2500 from its victims. These attackers used different techniques to bypass detection, like executing ransomware in memory, evading User Account Control, bypassing MOTW using .js files., etc.
Magniber requires administrative privileges so that the victim will not be able to recover its data, to gain administrative privileges the malware uses User Account Control bypass to execute commands withouting letting the victim know. The malware has a list of extensions and according to that it encrypts the files of the victim machine and leaves a ransom note in each directory.

Other red team strategies to bypass MOTW
1. Abusing software that does not set MOTW
Create a payload in a file format which is handled by software that does not set Zone Identifier information.
a. 7Zip
Manually extracting a file through 7zip other than double clicking the file will not set Zone.Identifier ADS.
b. Git client
Git clone does not create a Zone.Identifier ADS.
2. Abusing container formats
As Alternate Data Streams is an NTFS feature, Zone.Identifier ADS will not be created on other file systems, for example FAT32. Using that you can embed a payload in container formats such as .iso, .vhd, img and vhdx.
Blue team strategies
Mitigation
Disable auto-mounting of disk image file formats such as iso, vhdx, img and vhd.
Unregister container file extensions in Windows File Explorer.
Block container file types at web and email gateways.
Detection
Inspect and scan file formats eg: .gzip, arj, iso, etc. which are commonly abused by threat actors to bypass MOTW.
Monitor files that are extracted from archive/compressed and are downloaded from the internet. These extracted files may not contain the MOTW tag.
Reference:
Comments